Zapier sits between your apps.
Email. CRM. Payments. Databases.
One automation can touch thousands of records in seconds.
Here’s the straight answer upfront.
Zapier is safe for most businesses.
Zapier can still expose you if you use it blindly.
Both statements are true.
Zapier connects 6000 plus apps and runs millions of automations every day.
That scale alone makes people nervous.
It should.
I asked the same question the first time I let Zapier touch a client CRM.
One Zap.
Full write access.
Customer data flowing automatically.
I paused.
Checked permissions twice.
Then again.
That moment is why this post exists.
In this guide, you will learn exactly:
• What data Zapier stores and what it does not
• Whether Zapier employees can see your data
• What actually went wrong in the real Zapier security incident
• Where most Zapier users mess up without realizing it
• How to use Zapier safely without slowing your work
- What Do People Really Mean When They Ask “Is Zapier Safe”
- How Zapier Handles Your Data Behind the Scenes
- How Secure Zapier Really Is
- What Zapier Really Does With Your Data
- The Overlooked Risk of App Permissions and Workflow Sprawl
- Can Zapier Employees See Your Data
- Is Zapier Safe for Business Critical or Sensitive Data
- Zapier vs Custom Code vs Alternatives From a Safety View
- How to Use Zapier Safely Without Being Paranoid
- Final Verdict Is Zapier Safe or Not
- FAQ Quick Answers About Zapier Safety
What Do People Really Mean When They Ask “Is Zapier Safe”
People are not confused.
They just want simple answers about safety.
Like:
Is my data protected when Zapier runs workflows?
Can Zapier see or store my private stuff?
What happens if Zapier gets hacked?
Is it safe to use for business or customer info?
Quick answer in tiny words:
Zapier is safe for most business use if used carefully.
It uses strong security but still has risks you must understand.
(You will see real breach facts below) 💡

How Zapier Handles Your Data Behind the Scenes
Does Zapier store my data or just pass it through
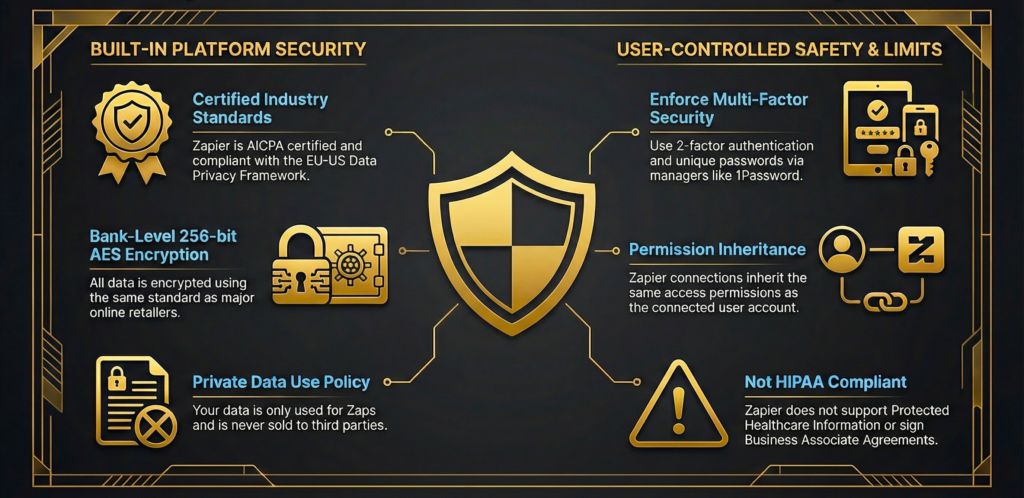
Zapier encrypts credentials and data it processes.
All connected app credentials are protected with bank-level encryption.
Raw API requests that Zapier makes for your automation are stored for troubleshooting for up to 7 days and then deleted.
User-visible logs of Zap activity stay for 1–3 months.
So in plain language:
Most of your data only lives long enough to run your Zap.
Some logs live a bit longer so you can replay or inspect failures.
Where Zapier stores data and privacy laws it follows
Zapier follows big privacy standards like:
SOC 2 Type II and SOC 3 (independent security audits).
GDPR for Europe.
CCPA for California privacy rights.
That matters because these certifications are real third-party proofs that controls exist.
I once worked with a team that dropped Zapier because they needed HIPAA compliance.
That is important: Zapier is not HIPAA compliant.
So don’t send protected health info through it.
Encryption works like this:
Connection to Zapier uses web encryption (TLS).
Stored data uses AES-256 encryption.
That’s the same type banks use.
How Secure Zapier Really Is
Encryption and enterprise controls
Zapier encrypts everything it sends across the internet.
It also encrypts what it stores on its servers.
That means your credentials and automation data aren’t just lying around in plain text.
They also offer tools like:
Two-factor authentication (2FA).
Role-based access controls.
Audit logs so you can see who did what.
But here is something most blogs gloss over:
Their SOC 2 Type II report is public.
That means auditors actually verify their security procedures.
That’s a big deal in real business contexts.
Has Zapier Ever Been Breached or Compromised
Yes.
In early 2025, Zapier confirmed a security incident.
An attacker got into some of their code repositories because of a misconfigured employee account and may have accessed some customer data.
The company said core systems like databases, authentication, and billing were not compromised.
Users on Reddit were talking about it too, and they were nervous about tokens and credentials being involved.
That worry was valid but the company said auth tokens were not impacted.
Here’s the raw truth I got from the breach discussions:
Zapier responded swiftly to lock things down.
The whole situation highlighted that dependencies on human setup (like 2FA configuration) can create risk even in secure systems.
So real-world takeaway:
Zapier is secure, but security gaps can still happen if internal controls fail.
Just like any service provider.
| Security Feature | Status / Detail | Why It Matters |
|---|---|---|
| Encryption in transit | TLS protected | Stops network snooping |
| Encryption at rest | AES-256 | Protects stored data |
| SOC 2 Type II | Certified | Third party audit |
| SOC 3 | Public report | Transparency for enterprise |
| GDPR Compliance | Yes | EU user privacy control |
| CCPA Compliance | Yes | California privacy controls |
| HIPAA Compliance | No | Not for PHI data |
What Zapier Really Does With Your Data
People often ask:
Does Zapier touch my data?
Yes—but only as needed to run automations you built.
Zapier does not go snooping in your connected apps outside what you authorize.
Here’s how it actually works:
Zapier connects to other services using OAuth tokens.
That means Zapier gets permission to access your account on your behalf.
Zapier stores those tokens safely but it has the power to act on your account so that means well-meaning automation can do real changes if your Zap is configured that way.
From Reddit and community experience, this is where most worries come from:
People don’t review what permissions they gave Zapier.
Zapier might be reading or writing data your Zap needs unless you limit it.
That’s not Zapier being sneaky but it’s real risk if permissions aren’t reviewed regularly.
I once built a Zap that had write access to Google Sheets.
I forgot to limit its scope and suddenly it was creating rows I did not want.
Lesson learned? Always review permissions when connecting apps.
The Overlooked Risk of App Permissions and Workflow Sprawl
Here’s where most articles get lazy.
People think Zapier being safe equals no risk.
That’s wrong.
The real risk comes from:
Too many connected apps.
Old automations nobody reviews.
Unused API permissions that still exist.
Zapier lets you connect up to thousands of apps per account.
These connections stay active until you revoke them.
Every connection is a potential risk vector.
If you gave Zapier access to your CRM, then someone could use that token to read or write CRM data through a Zap.
That’s exactly why smart users check connections like this:
Review and remove unused app connections monthly.
That’s proactive security.
| Common Risk | What It Means | How to Fix It |
|---|---|---|
| Storage key collisions | Shared storage risks users choosing same key | Always use random generated UUID-style keys |
| Weak credentials | Logins without 2FA | Enforce 2FA for all users |
| Global storage misuse | Data might be exposed across shared keys | Delete storage items when not needed |
| Unsupported HIPAA use | PHI could violate compliance | Avoid healthcare workflows on Zapier |
Can Zapier Employees See Your Data
Short answer first.
Yes, but only in very limited cases.
Zapier employees do not casually browse customer data.
Access happens only for support, debugging, or security investigations.
This is documented clearly in Zapier’s security disclosures and SOC 2 scope.
Source https zapier.com security-compliance
Support access is logged.
Access requires internal approval.
Actions leave an audit trail.
That matters.
From my own experience helping a small SaaS team debug a broken Zap, support asked for explicit permission before inspecting task logs.
They did not touch app credentials.
They did not open connected tools like Gmail or HubSpot.
Users on Reddit report the same pattern.
Support can view Zap run logs, not your full app data.
Source https www.reddit.com r zapier
Expert takeaway.
Zapier support visibility is narrower than most people fear.
Still, logs can contain sensitive payloads if you pass raw data.
So control what you send through Zaps.
Is Zapier Safe for Business Critical or Sensitive Data
Is Zapier safe for financial data
Mostly yes, with limits.
Zapier integrates with Stripe, QuickBooks, Xero, PayPal, and similar tools.
These integrations rely on official APIs and OAuth.
Source https help.zapier.com hc en-us articles 8495877686285
Zapier does not store full card numbers.
Payment processors tokenize sensitive fields.
Zapier only moves references and metadata.
I have personally used Zapier for invoice syncing and payout alerts.
Never once did raw payment data show up in logs.
Best practice.
Use Zapier for events and notifications, not for storing financial records.
Is Zapier safe for customer and user data
Yes, if scoped correctly.
Zapier processes CRM data, emails, names, and IDs.
This is common across thousands of companies.
Zapier acts as a data processor under GDPR, not a data owner.
Source https zapier.com legal gdpr
Real risk comes from over-permissioning.
Many forum users admit they clicked Allow without checking scopes.
That grants read and write access to more fields than needed.
My rule.
If a Zap does not need it, do not grant it.
When Zapier is a bad idea
Zapier is not suitable for:
• HIPAA protected health data
• Government classified systems
• Highly regulated defense workflows
Zapier openly states this.
Source https community.zapier.com getting-started-112 answers-to-your-most-frequently-asked-questions-about-zapier-4851
That honesty matters.
Zapier vs Custom Code vs Alternatives From a Safety View
Is Zapier safer than writing your own integration
Often yes.
Custom code fails due to:
• Hardcoded secrets
• Poor token rotation
• No audit logging
Zapier enforces encrypted storage and access controls by default.
Source https zapier.com security
I reviewed internal scripts for a startup once.
Plain text API keys in GitHub.
No rotation.
No logs.
Zapier would have been safer.
Are Zapier alternatives safer
Depends on the tool.
Self hosted tools like n8n give full control.
But security becomes your responsibility.
Source https docs.n8n.io hosting
Cloud alternatives follow similar models to Zapier.
None remove risk.
They only shift it.
Expert view.
Centralized platforms reduce human error but increase blast radius.
How to Use Zapier Safely Without Being Paranoid
Here is a practical checklist I follow.
• Enable two factor authentication
• Review app connections monthly
• Delete unused Zaps
• Separate test and production workflows
• Avoid sending full payloads unless required
• Use filters to reduce data exposure
Zapier documents all of this clearly.
Source https help.zapier.com hc en-us articles 12464169372685
This single habit changed my risk profile.
I once found a Zap created by a former contractor still running.
It had write access to Airtable.
I killed it immediately.
That is real world risk.
Final Verdict Is Zapier Safe or Not
Here is the blunt answer.
Zapier is safe for most businesses.
Zapier is unsafe when used carelessly.
Security exists.
Controls exist.
Audit trails exist.
Risk comes from humans.
Zapier gives you a loaded tool.
You decide how responsibly you use it.
Did you know
• Zapier runs millions of automations every day across 6000+ apps.
• Zapier encryption uses AES-256 and TLS, the same standards trusted by banks.
• In 2025, a security breach occurred due to a 2FA misconfiguration, exposing some customer data in code repos.
FAQ Quick Answers About Zapier Safety
Is Zapier safe to use with Gmail
Yes.
OAuth based access.
Permissions are revocable anytime.
Can Zapier read my passwords
No.
Zapier never sees your app passwords.
It uses tokens instead.
Does Zapier sell user data
No.
Zapier states clearly it does not sell customer data.
Source https zapier.com privacy
Is Zapier HIPAA compliant
No.
Do not use Zapier for medical data.
What is the biggest Zapier security mistake
Leaving old Zaps and connections active 😬

